
On February 24, the world devastatingly witnessed Russia’s official war launch against Ukraine.
This past Sunday, an FBI report called on the U.S. private sector to prepare for potential state-sponsored cyberattacks launched by Russia against Ukraine that can spill over into the U.S. New York is among the first states to take immediate action, with Governor Kathy Hochul announcing the state is revamping its cybersecurity preparedness efforts. “The reality is that because New York State is a leader in the finance, healthcare, energy, and transportation sectors, our state is an attractive target for cybercriminals and foreign adversaries,” said Hochul.
Cyberattacks fall under the traditional ‘umbrella’ categories of sabotage, espionage, and subversion. The Russian Main Intelligence Directorate (GRU) typically orchestrates these attacks, which often involve using customized malware (malicious software) to target the hardware and software underpinning a target nation’s systems and infrastructure. It is a cheaper and more rapid ‘weapon’ for modern-day wars. This week, Russian cyberattacks against Ukraine took place, including crashing several of Ukraine’s bank and government department websites.
The U.S. and its allies are supporting Ukraine. In a clear message to the United States and its allies, Putin warned foreign powers not to interfere in his operation: “If you do, you will face the consequences greater than any you have faced in history. All relevant decisions have been taken. I hope you hear me.” Cybersecurity is geographically limitless, and as such, both private and public organizations and citizens in the U.S. need to prepare for this new era of cyberwarfare.
In line with StrikeForce Technologies and Aite-Novarica’s proposed standards framework for U.S. video conferencing cybersecurity, the potential for cyberwarfare infiltration should be considered a Level-4 classification. Cyber threats against our Homeland Security are categorized as Level-4. These attacks are very high risk as they can compromise ‘sensitive and unclassified’ data in several private and public sector organizations, affecting the entire nation. As already seen with Ukraine, catastrophic consequences for such attacks by Russia can include malware attacks on banks and financial institutions (size doesn’t matter in this situation, both small and large organizations are at risk). Beyond financial ruin, Russia has already demonstrated its ability to cripple U.S. healthcare and energy software and hardware infrastructures.
Federal and state governments have still not yet created cybersecurity standards specifically for video conferencing tools, many of which can be easily breached by hackers. Combine this with the fact that remote video collaboration communications are ubiquitous due to the pandemic, so we urge organizations in the private sector to implement the following technical protocols proposed in the framework. These guidelines have been specifically created to protect private sector organizations, especially those in healthcare, finance/fintech, legal, banking, insurance, and enterprise, to be prepared to defend themselves against cyberwarfare.
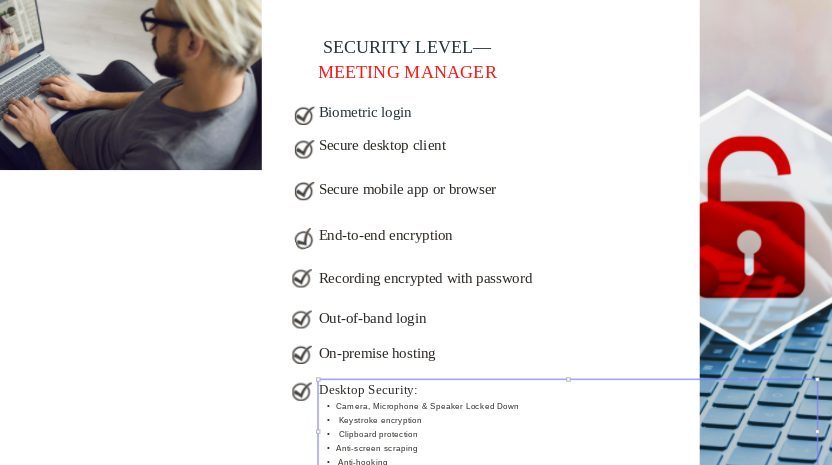
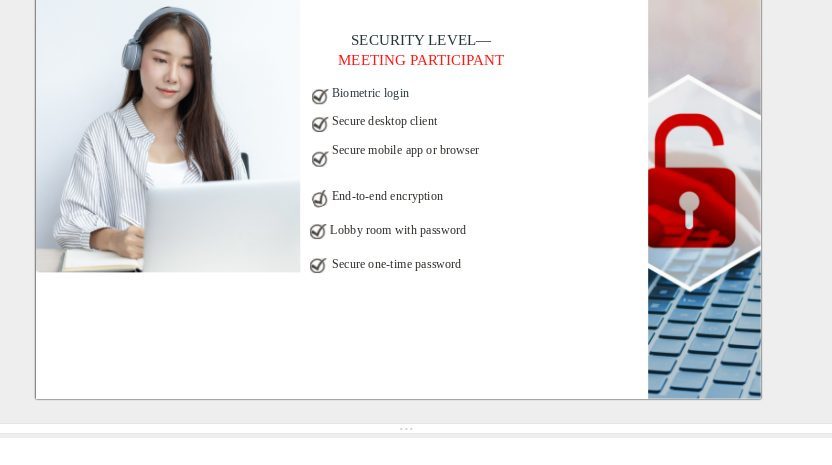
The complete framework can be downloaded free from our site.
